2025/26 Weekly Update from the EU ISAC for Cities & Regions: No Friday calls 12 & 19 Sep / Barista AI assessment of Regional Defence in Depth solution suite / Draft ENISA Threat Landscape 2025 report under review – your input? / AI threat by vendors themselves / Conference season approaching – see news section / Looking for Opportunity to conduct End-To-End Smart City Service Security Assessment
** For Back Issues see https://isac4cities.eu/blog **
The City ISAC (I4C+) is an Information and Analysis Centre whose members are IT and cyber security decision makers exchanging knowledge to improve their cities and collective cyber resilience. I4C+ is a Special Interest Group (SIG) hosted by Major Cities Europe (MCE). Dr. Oliver Schwabe is a member of MCE and in his function Chair of the ISAC for Cities Plus (I4C+). He is the person in charge of this effort on behalf of MCE and the responsible contact person. I4C+ is recognized by the European Agency for Cybersecurity ENISA. See https://isac4cities.eu/.
** Note there are no calls on Friday 12 and Friday 19 September **
Discussion Summary
Hi everyone, friends from Bulgaria, Croatia, Estonia, Germany, and Ireland joining this week.
We started off discussing the perennial challenge faced by one colleague in migrating legacy applications to the cloud – something we all deal with of course and since legacy (“technical debt”) is the key driver of security challenges, it is a good thing to do -> how to deal with what is too complicated / costly to migrate is something we need to think about carefully though since what we “leave behind” may become the “unlocked door” in any security infrastructure.
Another colleague shared the story of a security notification regarding leaked user data in the dark web -> two days of work to find out it was only user emails (no passwords) and that the data was not very fresh so that password renewal policies had probably covered the potential threat for logins, although the phishing vector is of course still relevant. Another nice example of needing to carefully evaluate threat intelligence for being “intelligent” before dedicating analysis time.
We then reflected on a question of a colleague on whether out-sourcing SOCs makes sense and agreed that while it seems a good thing to do, it does not alleviate the need to have an internal team that conducts remediation actions (assuming we are not talking about a third-party that also manages our infrastructure).
AI was also a subject of course and we reminded ourselves that while there are many good places to explore leveraging AI capabilities, anything related to formal communications with citizens is tricky due to potential legal ramifications. A human “airgap” in these communications is critical to avoid unnecessary litigation. This then got us to how many solutions (i.e. Acrobat) seem to have AI capability enabled and offered by default – disabling this needs to happen on a user level and then always ends up being re-enabled with updates etc. AI is being “forced” upon us and setting the stage for data breaches – we need to do more to protect our colleagues from mistakenly compromising themselves!
Finally, we also discussed how email is the fundamental problem and that some nations mandate it as a formal communication channel with citizens – no way around this therefore and although certified email providers can help, this is only about a delivery process and threat actors are targeting these providers as well. EIDAS https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:32014R0910 should be driving improvements here, however it remains a fragmented landscape (inter-) nationally.
Note that ENISA have reached out and requested our review of the draft ENISA Threat Landscape 2025 report. This has been shared with several colleagues from public administrations and if you are also interested in supporting, please let me know – feedback is requested by close of play September 11th. One comment already received from a colleague is “In my opinion, an important reason for the weaknesses in information security in our country’s public administration is the low budgets allocated for this purpose, the lack of dedicated staff, and inadequate training. Information security is approached with the mindset that “it can’t happen to me.” There is a significant discrepancy between the laws and their enforcement. The role of the central government needs to be changed here, so that it acts more as a consultant rather than a controller who only imposes fines.”
Conference season upon us with MCE Annual Conference, EU ISACs Summit, The North European Cyber Days, European TLD ISAC Conference, and EE-ISAC 26th Plenary. Check out news sections.
We also did an interesting exercise and asked our Barista AI whether he thought an example Defence in Depth solution set consisting of the following was effective and whether he thought there were any gaps: “Azure Hybrid Secure Access, Cisco Email Security, Cisco Email Security / NCSC Mailcheck, DigiCert, F5, FortiGate, FortiGuard, Kallidus Training, Maple SOC, Microsoft Always On VPN, Microsoft AppLocker, Microsoft Authenticator, Microsoft Azure AD, Microsoft Bitlocker, Microsoft Defender for EndPoint, Microsoft Sentinel, Nessus Manager, PSN Accreditation , and Smoothwall Web Filter.” Note that the solution set was previously provided by an EU region.
“Your proposed Defence in Depth (DiD) solution set is comprehensive and covers multiple layers of security—from identity and access management to endpoint protection, network security, and monitoring. Below is a structured analysis of its effectiveness and potential gaps:
Strengths of Your Solution Set
1. Identity and Access Management (IAM)
- Microsoft Azure AD: Centralized identity management, MFA, and conditional access.
- Microsoft Authenticator: Strong MFA for user authentication.
- Azure Hybrid Secure Access: Secure access to hybrid environments (on-prem + cloud).
2. Endpoint Protection
- Microsoft Defender for Endpoint: Advanced threat protection, EDR, and vulnerability management.
- Microsoft BitLocker: Full-disk encryption for data at rest.
- Microsoft AppLocker: Application whitelisting to prevent unauthorized software execution.
3. Network Security
- FortiGate/FortiGuard: Firewall, intrusion prevention, and web filtering.
- F5: Load balancing, DDoS protection, and application security.
- Smoothwall Web Filter: Content filtering and web security.
4. Email Security
- Cisco Email Security: Anti-phishing, malware protection, and email encryption.
- NCSC Mailcheck: UK government-backed email security standards and compliance.
5. Monitoring and SOC
- Microsoft Sentinel: SIEM, threat detection, and incident response.
- Maple SOC: Managed SOC services for 24/7 monitoring.
- Nessus Manager: Vulnerability scanning and patch management.
6. Compliance and Training
- PSN Accreditation: Ensures compliance with UK Public Services Network standards.
- Kallidus Training: Security awareness training for employees.
7. Certificate Management
- DigiCert: PKI and certificate management for secure communications.
Potential Gaps and Considerations
1. Zero Trust Maturity
- Gap: While Azure AD and Authenticator are strong, a full Zero Trust Architecture (ZTA) requires continuous verification, least-privilege access, and micro-segmentation.
- Recommendation: Consider integrating Microsoft Entra Private Access or Zscaler Private Access for granular access control.
2. Cloud Security Posture Management (CSPM)
- Gap: No explicit mention of tools for cloud misconfiguration detection (e.g., Azure Policy, Prisma Cloud).
- Recommendation: Add Microsoft Defender for Cloud or Palo Alto Prisma Cloud for CSPM.
3. Data Loss Prevention (DLP)
- Gap: No dedicated DLP solution for sensitive data protection (e.g., Microsoft Purview DLP).
- Recommendation: Integrate Microsoft Purview for data classification and DLP.
4. Third-Party Risk Management
- Gap: No tools for vendor/supply chain risk assessment (e.g., SecurityScorecard, BitSight).
- Recommendation: Add a third-party risk management platform.
5. Backup and Disaster Recovery
- Gap: No mention of immutable backups or disaster recovery solutions (e.g., Azure Backup, Veeam).
- Recommendation: Ensure backups are encrypted, immutable, and tested regularly.
6. Insider Threat Detection
- Gap: While Sentinel and Defender for Endpoint help, a dedicated insider threat detection tool (e.g., Microsoft Purview Insider Risk Management) could add value.
7. OT/IoT Security
- Gap: If applicable, Operational Technology (OT) or IoT security is not addressed.
- Recommendation: Consider Fortinet OT Security or Palo Alto IoT Security.
Summary Table: Coverage and Gaps
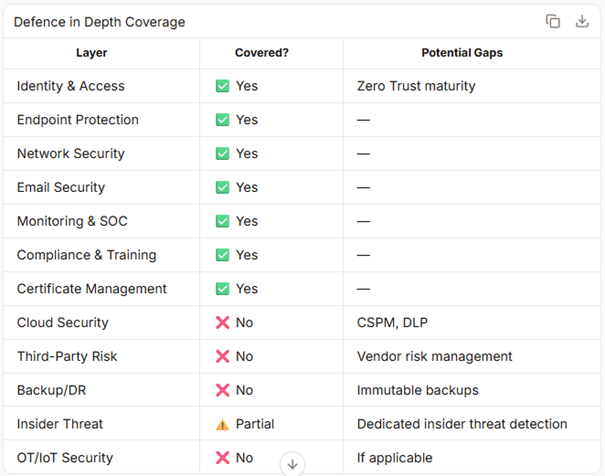
Final Thoughts
Your solution set is highly effective for most enterprise environments, especially with its focus on Microsoft and Cisco ecosystems. The gaps identified are context-dependent—if your organization handles sensitive data, operates in the cloud, or has third-party risks, addressing these areas will further strengthen your posture.”
One next step to leverage the above could be to ask Barista AI how the solution suite could be best configured to protect against specific indicators of compromise.
Cheers,
Oliver
| In the News |
- Major Cities of Europe, in collaboration with the City of Issy-les-Moulineaux, is pleased to announce the joint 2025 conference under the theme of “Piloting Disruptive Innovation in Cities and Regions”, which will be hosted at the UGC Congress Centre from October 9 to 10. Integrated into the Greater Paris Metropolis, Issy-les-Moulineaux is one of the most innovative cities in France and has long been recognized as a leader in digital innovation, circular economy, and environmental footprint reduction. The event is co-organized with Issy Media, the public company responsible for communication and innovation in Issy-les-Moulineaux. The conference will be conducted in English and French, with simultaneous translation available. See www.majorcities.eu for more details.
- EU ISACs Summit, 10–11 November 2025, Athens: ENISA is pleased to announce the 2025 edition of the EU ISACs Summit, which will take place on 10 November (afternoon) – 11 November (full day) at ENISA premises in Athens. As in previous years, we plan to dedicate the first day to hearing updates and future plans, and the second day to a more interactive session or exercise. With plenty of time ahead, we would love to hear your ideas and suggestions for the agenda. Please share your input with us by 19 September.
- The North European Cyber Days: ECSO is proud to announce a new major event designed for the European Cybersecurity Community: The North European Cyber Days, taking place on 4, 5 & 6 November 2025 at the Oslo Science Park, Norway. This high-level event will bring together key stakeholders from across cybersecurity, artificial intelligence (AI), and critical sectors to explore shared challenges, foster cross-border collaboration, and unlock new opportunities for investment, innovation, and resilience in Europe’s digital landscape.
- INVITATION to the 2025 European TLD ISAC Conference: Our friends at TLD ISAC are delighted to invite you to their 2025 edition of the European TLD ISAC Conference, which will take place on 20 November in Brussels. Under the overarching theme “Ensuring cyber resilience amidst shifting threats and geopolitical realities”, we will hear voices from across the political, policy, technical and operational spheres. Attendees will gain insights into how European stakeholders view and deal with the challenges arising from the unpredictable geopolitical situation and why collaboration is more important than ever. In our tech-focused sessions, speaker will dive into attack simulation and response strategies, intel sharing and monitoring practices, malware detection and vulnerability management approaches. As this is an invitation-only event, we encourage you to register early to receive the latest updates. If you are interested in joining, please contact me for registration details.
- EE-ISAC 26th Plenary: Celebrating 10 years of cybersecurity collaboration! 29 October 2025 | Brussels, Belgium. We are excited to announce that the EE-ISAC will host its 26th Plenary on October 29, 2025, in Brussels. This event will be especially significant as it marks EE-ISAC’s 10th anniversary – a full decade of empowering the European energy sector with collective cybersecurity knowledge, trusted partnerships, and strategic resilience. This is a face-to-face event and by invitation only. If you are interested in joining, please contact me for registration details.
Looking for Opportunity to conduct End-To-End Smart City Service Security Assessment
As part of some exploratory work, we are looking for an opportunity to conduct an end-to-end security assessment of an active Smart City Service. At this stage we would apply for national NCC FSTP grants via a trusted SME and in partnership with the administration. Some details below and please reach out to me if you are interested in learning more – need someone on your side that can help evaluate the service please.
The outcome would be something similar to the below template where:
1. All IT assets supporting the service are identified,
2. The security of the assets is assessed (using https://www.cisecurity.org/controls/v8-1),
3. Actions to improve the end-to-end security are identified (item and Defence in Depth level) and prioritised, and
4. the (anonymised) results / recommendations are validated with other members of our community.
The IT assets are then held in our ISAC MISP and threat intelligence for these assets monitored / managed there. Data security provided via permissions management and an MoU would of course also be needed.
In a further stage we could look at how to leverage AI to help in identifying actionable items / manage these to closure.
We would then also look to map the results into control frameworks that you use locally/regionally/nationally, and of course NIS2/CIS18 etc.
We aspire to use the experience to build a robust pilot and, if benefits are visible, to identify local/regional/national/EU funding sources to grow.
The benefit for participants is (a) the additional resources we provide (b) improving the security of Smart City projects, and (c) the opportunity to learn how others are tackling specific IT asset (and end-to-end) security.
| ISAC Services (Member Funded) |
We have published our services at Services Offered – EU ISAC for Cities (isac4cities.eu). Please do review and consider reaching out to include such in your activities and budgets.
Note that emerging new services are related to managing the MISP platform (and onboarding) plus Barista.
Please remember you can reach the whole group via city-isac-i4c-tlpwhite@majorcities.eu. A dedicated group for those cities signing the NDAs is available separately.
Also note our LinkedIn organisational page at https://www.linkedin.com/company/eu-city-information-sharing-and-analysis-center-isac/ and our discussion group at https://www.linkedin.com/groups/12773643/. Do follow us / join.
Join our weekly Friday morning coffee chats from 9am-10am CET – feel free to come in your pyjamas. Let me know if you are missing an invite and I will send.
Thank you for the support, your City ISAC I4C+ Team.
Cheers and ever onwards
Oliver
Innovating our Future… Together
Chair City ISAC I4C+ / Dr. Oliver Schwabe.
Email: oliver.schwabe@isac4cities.eu Mobile: +49 (0) 1709053671. Web: https://i4c.isacs.eu/ & https://www.majorcities.eu/isac-for-cities-plus/