2024/34 Weekly Update from the MCE SIG “City ISAC I4C+” Highlights: No call next week / Cyber MUST clearly support the strategic roadmap of the administration / Example Opportunity Dimensions & simplified PID / ISAC Baseline with first Full Users / Supplier Bow-Tie example / Experiences with EU Digital Identity Wallet? / Open Source solutions may well be commercialised / Remember Cyber Awareness Month
** No call next week due to parallel ENISA Multi ISAC Summit in Athens **
** For Back Issues see https://isac4cities.eu/blog **
The City ISAC (I4C+) is an Information and Analysis Centre whose members are IT and cyber security decision makers exchanging knowledge to improve their cities and collective cyber resilience. I4C+ is a Special Interest Group (SIG) hosted by Major Cities Europe (MCE). Dr. Oliver Schwabe is a member of MCE and in his function Chair of the ISAC for Cities Plus (I4C+). He is the person in charge of this effort on behalf of MCE and the responsible contact person. I4C+ is recognized by the European Agency for Cybersecurity ENISA. See https://isac4cities.eu/.
| Weekly [TLP:RED] |
Please contact us directly for more information – these are summaries only and the “key” is in the actual stories shared privately. The stories are based on personal sensitive knowledge shared by peers in personal conversations under Chatham House Rules. This “stuff” may look obvious (?) – the magic lies between the lines and only becomes visible in a personal conversation.
This week´s thoughts are based on the scope of essential services your public administration subscribes to, operates, and manages, including what IT systems support their delivery.
- Weekly [TLP:RED] for Publicly Elected Officials (Repeat – 3): Ensure you have a communication professional trained in handling the media during a cyber incident available and delegate ALL communications to them immediately.
- Weekly [TLP:RED] for Essential Services Managers (Repeat – 3): Talk to the IT Help Desk, make sure they have a list of “super users” of your systems and treats them as “VIPs” when they call (or make sure they are considered as your official delegates).
- Weekly [TLP:RED] for IT Leaders (Repeat – 3): IT service outages due to cyber incidents are usually the best “sellers” for improved budgets. It can make sense to choose a “reactive armour” strategy in some spaces – let “contained” breaches occur…
| Summary |
Hi everyone, I hope you are doing well. Four cities / regions joining from Belgium, Bulgaria, Estonia, and Italy, on Friday morning and one member sharing the story on how busy they are preparing for an announced NoName attack during their local and regional elections this weekend – thumbs pressed for them that nothing significant occurs.
We initially looked at how any cyber security strategy needs to align to the strategic roadmap of the administration (see examples at https://www.pratocircularcity.it/it/next-generation-prato/documento-strategico/pagina1942.html and https://strateegia.tallinn.ee/en/vision). It needs to be risk based and always explore how different levels / elements Defence in Depth https://blog.knowbe4.com/hubfs/Defense_in_Depth.jpg?t=1534692189594#keepProtocol can leverage each other as supporting Opportunities and Threats, i.e., a threat in identity management of critical processes supporting the strategy, might be addressed more cheaply / effectively through micro-segmentation of network services. Opportunities are sort of like the opposite of building higher walls, sending out the cavalry via a side-gate instead! Their business case is cost-savings in cyber which is perhaps always of interest as IT costs continue to explode (remember that some member experiences suggest that for every €1 spent on IT, you need to spend another €3 at least for securing it.
In respect to opportunities, we then looked at examples from a Risk Opportunity Checklist for Suppliers from a large commercial organisation. Maybe interesting as orientation since opportunities need to be managed just as rigorously as threats in your risk management system:
- Technical: Simplification/removals of Requirements, Simplification of Assumptions, Clear & simplified acceptance criteria, Re-use of proven & mature technologies, Simplification and/or reuse of technical interfaces, Relax tolerances, Maximise reuse of components, Alleviation of tests & qualifications (replace by analysis), Use of simulations instead of real tests, Anticipation of tests, Maximise interchangeability.
- Organisation: Set-up efficient project organization, Set-up efficient & lean Project monitoring methods & tools, Optimize Roles & responsibilities with Supplier, and remove redundancies., Anticipation of key decisions, Use of Collaboration tools, to allow an efficient communication with Supplier, and sharing of information, Identify and use best practices from both companies, Best use of synergies between Projects / Programmes (e.g. skills, shared means & tools), Anticipated availability of key inputs & enablers, Use of E2E integrated planning, Early involvement of Support teams to integrate In Service feedback in the development.
- People: Optimize use of resources (Project Mgt, engineering, blue collars,…), Identification and best use of specific skills, Use of less busy periods to perform trainings.
- Supply Chain & Logistic: Optimization of supply circuits / transport / logistic systems; Optimization of logistic flow to limit need of storage capacity, Use of experienced & robust Tier2 Supplier / subcontractor
- Processes & Tools: Re-use of mature and proven processes & tools, Optimization of processes for better efficiency, Take benefit of new tools and technologies (digitalization…), Use tools obsolescence as a driver to implement more efficient tools, Connection of Airbus & Supplier tools, Implement tools redundancies & fail safe IT infrastructure
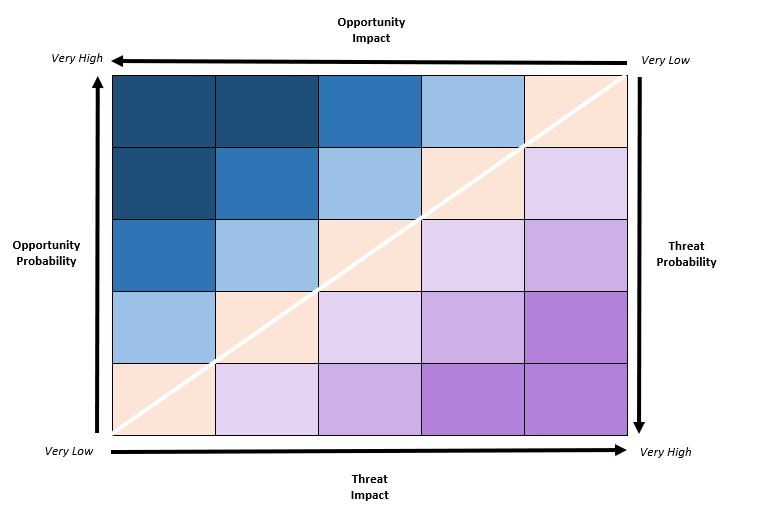
This week´s image is self-generated – a suggestion for a simple image to tell your risk (opportunities and threats story.
Perhaps interesting as well was some bow-tie worked shared by a colleague regarding a successful attack on a key supplier of a public administration. Key risk threats were: Supplier no longer financially solvent, Supplier impacted by disasters (i.e., flooding), Supplier impacted by cyber attack, and a supplier of a supplier fails. Key Preventative Controls: Onboarding assessment, Clear definition of delegated authority, Robust process documentation, Regular and robust quality assurance / performance reviews, and Shared risk register. Key Detective Controls: Continuous monitoring, Regular financial reviews, Contingency planning (with alternate disaster recovery source), Robust process documentation, Maintained lessons-learned, Robust business continuity plan, and Relevant insurance. Key Impacts: Employee dissatisfaction, Service disabled, Penalties / fines / legal damages, Reputational loss, and Increased costs for disaster recovery / supplier change.
Before I forget – asking on behalf of a colleague – what are your experiences in realising the EU Digital Identity Wallet according to the eIDAS 2 regulations (see also https://www.enisa.europa.eu/news/eu-digital-identity-wallet-a-leap-towards-secure-and-trusted-electronic-identification-through-certification)? Please do reach out to me if you can share since this is one area of focus we will be exploring more in future as well.
Remember also it is Cybersecurity Awareness Month and CISA has yet again launched some very helpful activities / tools see https://www.cisa.gov/resources-tools/resources/secure-our-world-resources-cybersecurity-awareness-month-2024-toolkit with the aim of reinforcing the four key behaviours:
- Use strong passwords and a password manager
- Turn on multi-factor authentication
- Recognize and report phishing
- Update software
Cheers,
Oliver
Insights from AI
I was curious about the opinion of Microsoft CoPilot about the probability of open source software solutions being commercialised. The AI responded as per below:
“The commercialization of open source software (OSS) solutions is becoming increasingly common. Many organizations are leveraging OSS to drive innovation and reduce costs. According to the 2024 State of Open Source Report by OpenLogic, open source adoption is on the rise across various industries, from early-stage startups to large enterprises. While it’s difficult to assign a specific probability, the trend suggests that a significant number of OSS solutions will continue to be commercialized as businesses recognize the benefits of open source technologies. This includes operating systems, cloud-native software, databases, and security tools”
| In the News |
- ENISA Promoting security in the digital world during the European Cybersecurity Month https://www.enisa.europa.eu/news/promoting-security-in-the-digital-world-during-the-european-cybersecurity-month. This year’s campaign theme is social engineering, a prevalent cybersecurity threat in the digital landscape.
- Applications are open: ENISA Cybersecurity Support Action Programme tender procedure https://www.enisa.europa.eu/news/applications-are-open-enisa-cybersecurity-support-action-programme-tender-procedure.
- Cyber attack on a association of municipalities in Germany https://www.elbe-heide.de/news/1/987561/nachrichten/eingeschr%C3%A4nkte-erreichbarkeit-der-verwaltung-der-verbandsgemeinde-elbe-heide.html
- American Water shut down some of its systems following a cyber-attack https://www.sec.gov/Archives/edgar/data/1410636/000119312524233300/d869346d8k.htm
| City ISAC Services (Member Funded) |
We have published our services at Services Offered – EU ISAC for Cities (isac4cities.eu). Please do review and consider reaching out to include such in your activities and budgets.
The ISAC Baseline now has its first fully participating administration. The ISAC Baseline offers the following questionnaires for the organization’s status assessment and benchmark against other participants:
- EU cyber awareness survey (ISAC specific awareness survey for relevant roles)
- CIS18 cyber essentials (IG1)
- NIS2 questionnaire
- CIS18 full questionnaire (IG3)
- When accessible, the ISAC Baseline will include ENISA’s Minimum Requirements for operators of essential services
All questions are mapped to relevant requirements and best practice standards , meaning comparable requirements across standards are mapped to the same questions making it easy for compliance officers and cybersecurity managers to evaluate compliance: “One assessment comply many”.
All questions are mapped to NIST CSF (Security Functions) making analysis of security performance and the maturity of organizations is evaluated using NIST TIER groups.
The Benchmark is available to all participants and selected peers, change processes are supported by Benchlearning, which allows participants to share experience on best practice solutions and -processes.
Please contact me if you would like to pilot.
| Project “PHALANX” – 2024 Multi-ISAC Tabletop |
You might remember that our City ISAC is a founding member of the EU Council of ISACs where we have many EU ISAC members from sectors like health, energy, finance, water, energy etc. As part of the work with the EU Council of ISACs we are also building out our relationship with ENISA. ENISA is planning a face-to-face Multi-ISAC event in October and we, the City ISAC, have an opportunity to run a 120 minute tabletop with many ISACs in the room plus a wide range of ENISA representatives in the morning of the second day. The tabletop will address all ISACs in the room and be based on a public administration being breached and asking for the support of the community to help tackle the challenge. The exercise will address all NIS2 domains and offer the ISACs a chance to jointly help. The context will be “The City of Fantasia operates, subscribes to and manages services for its 600k citizens in the sectors of: Public Administration (Operate), Energy (Manage), Transport (Manage), Healthcare (Manage), Drinking Water (Manage), Wastewater (Manage), Emergency Services (Manage), Digital Infrastructure (Subscribe), and ICT Service Management (Subscribe). The City has a regional airport, an industrial harbour and three major industrial production sites (chemicals, automotive, and battery).” -> then a professional actor appears with a thunder run strategy to make citizen life very uncomfortable!
Overall Agenda: EU ISACS SUMMIT 2024
ENISA organises the 2024 edition of the EU ISACS Summit, which will be held on 17-18 October in Athens, at ENISA premisses. The objective of the summit is to allow key representatives of various EU ISACs meet in person and exchange knowledge and information on their activities, successes and challenges as well as have an opportunity to meet with ENISA staff and learn about our work, including but not limited to implementation of NIS2, threat intelligence and information sharing as well as cyber exercises.
DAY 1 – 17 OCTOBER
12:00 – 13:00 Lunch at ENISA
13:00 – 13:15 Summit opening: Role of ISACs in the context of the NIS2 Directive
13:15 – 13:30 Keynote European Commission
13:30 – 15:00 Roundtable: Updates from each ISAC (5 minutes each), followed by a discussion on ISACs’ future plans and their potential
roles in NIS2 and sector-specific regulations
15:30 – 16:00 Maturity and criticality of NIS sectors – 360 assessment
16:00 – 16:30 Threat intelligence information sharing tools available from ENISA
16:30 – 17:00 Discussion: Challenges associated with information sharing (threat intelligence, incident reporting)
DAY 2 – 18 OCTOBER
9:00 – 9:30 The European Cybersecurity Competence Centre: exploring funding opportunities and avenues for cooperation
9:30 – 10:00 Overview of ENISA’s exercise platform and reuse of ENISA’s resources for ISAC’s exercise activities
10:00 – 12:00 Tabletop exercise: a scenario engaging all ISACs
12:00 – 12:30 Summit closing
Please remember you can reach the whole group via city-isac-i4c-tlpwhite@majorcities.eu. A dedicated group for those cities signing the NDAs is available separately.
Also note our LinkedIn organisational page at https://www.linkedin.com/company/eu-city-information-sharing-and-analysis-center-isac/ and our discussion group at https://www.linkedin.com/groups/12773643/. Do follow us / join.
Join our weekly Friday morning coffee chats from 9am-10am CET – feel free to come in your pyjamas. Let me know if you are missing an invite and I will send.
Thank you for the support, your City ISAC I4C+ Team.
Cheers and ever onwards
Oliver
Innovating our Future… Together
Chair City ISAC I4C+ / Dr. Oliver Schwabe.
Email: oliver.schwabe@isac4cities.eu Mobile: +49 (0) 1709053671. Web: https://i4c.isacs.eu/ & https://www.majorcities.eu/isac-for-cities-plus/