| Weekly Update from the “City ISAC I4C+” Highlights: New [TLP:RED] Guidance / Always Change Default Passwords on IT Assets / Ask Criminals to Pay your Ransomware? / Annual Reset of External Network Access? / “Grump-O-Grams” give satisfaction [TLP:WHITE] Dear all, New header to our updates – let us give this a try. The following suggestions are [TLP:RED] because they are honest comments by peers they would probably never acknowledge the statement officially: ********************************************************************************************** Weekly [TLP:RED] – Weekly [TLP:RED] for Publicly Elected Officials: When a cyber incident occurs, immediately call your lawyer to ensure you have someone to talk to under client / attorney privilege. – Weekly [TLP:RED] for Essential Services Managers: The higher the cyber-risk is on the risk register, the more likely an upgrade to your systems will be funded. – Weekly [TLP:RED] for IT Leaders: Put “VIPs” in a dedicated and separately protected network segment – their use of technology assets cannot be trusted to follow policy. ********************************************************************************************** Hi everyone and hope you are well – three cities and two regions stopped by on Friday morning. Got off to a silly start looking at a new GoogleMeet filter “on the beach” which projects a big floppy straw hat and sun-glasses onto the participant – worth a try if you are in a GoogleMeet and hey, we all need a laugh now and again… cyber is rough enough. Then we swapped some stories around how easy it is to hack webcams and perhaps observe passwords written down or entered into a keyboard. The key is that the default passwords on many wifi-routers and webcams are never changed by the buyers… these are then often in publicly available documentation or on boxes that might be easily accessible. When did you last renew passwords on assets like this? For general tours of open webcams see http://www.insecam.org/ and if you want to find insecure ones Shodan is the most popular general application. We were then given a nice tour of how to quickly create a live video presentation of illegal dumping in a city (“fly tipping”). It was amazing to watch a colleague use (the paid) version of ChatGPT to load some basic data on fly-tipping sites in their district and, within minutes, get a map / list of Google Streetview sources that allow for looking at these. Hmmm…. Maybe this could be expanded to find open webcams to do the same? Point though is this sort of “report” was done in minutes and was “good enough” for most presentation purposes…. One member then shared a recent experience of their organisation updating their access policies / whitelist to remove a large amount of unknown accounts / IPs as part of improving control over third party access. This of course resulted in dozens of suppliers losing access and then needing to go through the formalities of requesting renewed access. A “planned” event although the extent was a lot more significant than expected. Underlying this however the question of do we know who has access to our networks? Good practice is to evaluate this in depth quarterly by the way – and security tools can only identify the technical access, not understand whether that access is approved and doing approved things. We finally put a word to probably the only thing we can really do to express our dissatisfaction with supplier – the “Grump-O-Gram” which is a message expressing sever dissatisfaction with services. Coupled with simply delaying payment it is a way of at least inflicting some pain on the supplier since in most cases we are not really able to terminate contracts, or if we did, the supplier would really not be bothered. Does not change the quality of a service but does give some inner satisfaction we agreed. UPDATES In the News: If you are wondering how Antwerp is doing after a major cyber attack last year check out https://www.reddit.com/r/belgium/comments/13t5q90/hows_it_going_with_the_cyber_attack_recovery_in/. One interesting comment in the chat of this article is that third-parties (like criminal associations) might may a ransomware fee to just regain access to the data sources they need for their business – never thought of that…. City ISAC Services (Member Funded): A colleague carried out a feasibility study of installing the Community Edition version of the OpenVAS vulnerability assessment scanner starting from the source files. He followed the instructions in the url https://greenbone.github.io/docs/latest/22.4/source-build/index.html. He managed the installation on an Ubuntu 22.04.3 LTS virtual machine and patched some steps as packages were indicated that were not present. A separate security assessment of the software then however suggested multiple weaknesses and some questions on the licensing for commercial use. Remember that if you install free software on your networks, you are also installing security weaknesses in one way or another (plus commercial liabilities if you do more than pilot). Just don´t do it – buy the software from established vendors to at least have legal liabilities covered by the software contracts (and yes, you need to read the fine print there as well). If you want to pilot things – let us know and we can organise safe testing environments that may not be connected to your networks, but ensure you are not opening additional security windows. Project “DAVID” (Member Funded): The survey invitations to public officials heading up public administrations are coming along well – lots of fine-tuning as we set out to follow the established official routes for requesting participation AND being allowed to quote / indicate which administration is taking part. We will start piloting as soon as “MEET” is officially launched since the reference to such a project is typically quite helpful in increasing participation. Project “MEET” (EU Funded / Beneficiary): Based on https://www.enisa.europa.eu/topics/national-cyber-security-strategies/information-sharing/isacs-toolkit/view we review our current and desired maturity as per radar chart – a lot to do and waiting impatienty for the final paperwork to go through! 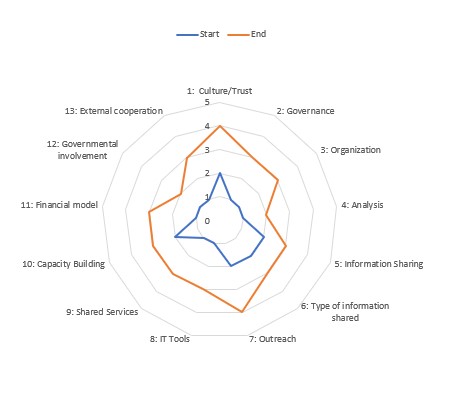 Project “VAUBAN”: No updates. Please remember you can reach the whole group via city-isac-i4c-tlpwhite@majorcities.eu. A dedicated group for those cities signing the NDAs is available separately. Also note our LinkedIn organisational page at https://www.linkedin.com/company/eu-city-information-sharing-and-analysis-center-isac/ and our discussion group at https://www.linkedin.com/groups/12773643/. Do follow us / join. Join our weekly Friday morning coffee chats from 9am-10am CET – feel free to come in your pyjamas. Let me know if you are missing an invite and I will send. Thank you for the support, your City ISAC I4C+ Team. |